For those of you that have seen talk on Identity 2.0 (OSCON or Web 2.0), you may recall a slide saying:
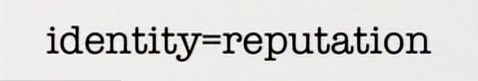
Marco at Clipperz had the graphic above from my talk in a post saying Identity is not reputation. He references Phi Windley’s post Owning Identity, Not Reputation or Transactions.
Looks to me like we are disagreeing on what is identity. A key point in my Identity 2.0 talk is that identity is all the things about me. Here are some definitions from dictionary.com:
identity: The collective aspect of the set of characteristics by which a thing is definitively recognizable or known
reputation: A specific characteristic or trait ascribed to a person or thing
To me, this makes it clear that reputation is part of your identity. Phil states that identity data is not transaction data or reputation data. I think it is. An example of transaction data being identity: “I’m the guy that bought that black sweater yesterday.”
Reputation is a bit trickier to understand as there are a few meanings to the word. Using the definition above, it is clear (to me :) that a characteristic ascribed to a person is reputation. Dick is tall. Dick is male. I take a broad view of what I mean by reputation. It is what any third party says about me. I see this as identity, since this is how that third party is identifying me. It may also be useful to other parties, if they trust that third party. If it is useful to other people, then it is valuable for me to be able to move that identity data around.
This brings us to how this topic got started at Clipperz, who are working on solving comment spam, just like we are at sxore. If Site A is able to determine that it is unlikely I am a spammer, and if a Site B trusts that Site A’s process for determining I am not a spammer, then it is useful to myself and the Site B to move that reputation from Site A to Site B, so that Site B does not have to start from scratch to determine I am not a spammer.


12 comments
February 11, 2006 at 11:11 am
February 11, 2006 at 2:54 pm
Trackback from Anonymous
February 13, 2006 at 3:37 pm
February 14, 2006 at 6:46 pm
Janine White
I enjoyed the presentation, but I disagree with this notion of identity because it confounds authentication and authorization. Read my blog entry, identity
February 15, 2006 at 9:39 am
We convey identity for many more things then just authentication, which is the process of proving the identity of a user. One important aspect of identity is what other people say about you. A good word to describe that is reputation.
Not sure why you think I am confounding authentication with authorization. I think I am clear in my drivers license example the seperate aspects of what happens in an identity transaction.
February 15, 2006 at 11:51 am
Janine White
Since the comment I left errored and didn’t leave a link to my blog entry, I’m not sure if you read it. The blog entry is here: http://jiwhite.blogspot.com/2006/02/identityreputation_14.html
February 15, 2006 at 12:03 pm
Janine White
In your definition of identity, you are including both who someone is (being) and their reputation. However authentication establishes who someone is, while authorization gives privileges based on trust and reputation. In a secure environment, authentication is completed first to uniquely identify an individual, then authorization can be applied to give that individual the appropriate level of privileges in the environment. By trying to fit both being and reputation in one conept, identity, the two are confounded, leading to a high likelihood of an insecure environment.
February 16, 2006 at 12:15 am
You don’t need unique identity for authorization, you need to know if the user has a role which, which I say can be thought of as reputation. You must be 21 or over to access a porn site. You must be subscriber to view some newspaper web sites.
Don’t take this the wrong way, but I think you are still stuck in an Identity 1.0 mindset!
February 16, 2006 at 7:00 am
Janine White
I guess that I’m not getting what makes this 2.0, instead of 1.0. It sounds like you’re describing Microsoft Active Directory, but calling it something else. Users have roles or groups within a directory which determine their permissions. Directories can trust each other to provide roles or permissions. Is Identity 2.0 any different from this theoretically, other than that it is not owned by Microsoft?
February 17, 2006 at 12:08 am
Roles and groups is not an Active Directory concept — pretty well established Identity management concept. Identity 2.0 is about how that information flows. In Identity 1.0, you prove you are a particular account, then the resource looks in the directory to see what roles you have, then makes a policy decision. In Identity 2.0, the resource says "here are the role(s) you need to have". The user then presents a set of role(s), the resource checks that those role(s) comply and makes an authorization decision.
Sounds like I need to explain this better in future talks.
March 31, 2006 at 10:30 am
transient
identity≠identification
identity>identification
March 31, 2006 at 10:32 am
true